Vendor
[SOLVED] SEC370 LAB 5 POLICY PAPER: Review the Network Attacks tutorial in the lecture. Submit a three- to five-page (800–1,200-word) security policy write-up for the antivirus, spyware, and adware policies…
[SOLVED] SEC370 LAB 4 DISABLING UNNECESSARY SERVICES: Exercise 1 – Disabling Unnecessary Services In this exercise, you will disable unnecessary services for laptops that are taken by users outside of…
SOLVED] SEC370 LAB 3 YOU DECIDE ACTIVITY: Review the Public Key Infrastructure, Hashing and Digital Signatures, Cryptography: Public Key Encryption, and Cryptology tutorials in the lecture. Go to http://nmap.online-domain-tools.com/, and…
[SOLVED] SEC370 LAB 2 CREATE FIREWALL RULES: In this exercise, you will configure Inbound and Outbound Windows Firewall rules. Please refer to your course material or use your favourite search…
[SOLVED] SEC370 LAB 1 YOU DECIDE: Perform reconnaissance on a target company of your choice using Google, their website, Whois, and nslookup to find out where the company is; who…
[SOLVED] FUNDAMENTALS OF PYTHON CHAPTER 9 PROJECT 1 2: 1. Write a GUI-based program that implements the bouncy program example discussed in Section 9.1.
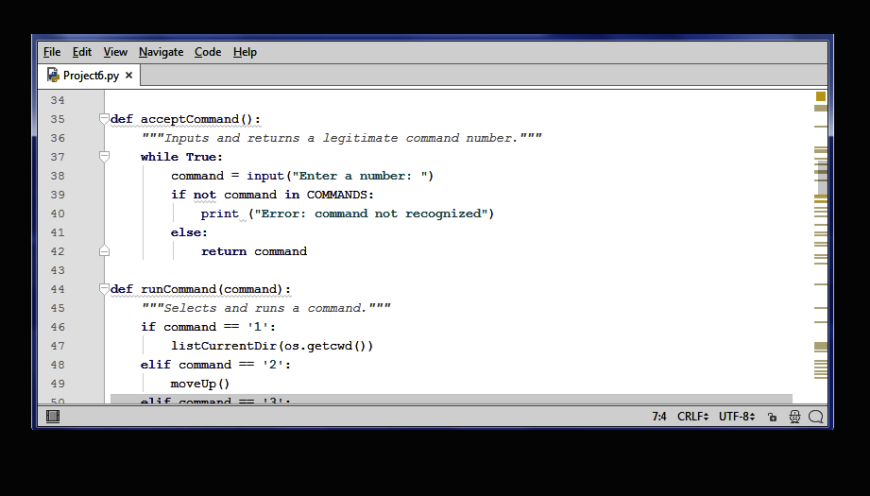
[SOLVED] FUNDAMENTALS OF PYTHON CHAPTER 6 PROJECT 6 7 8 9: These projects must be done in the latest version of IDLE: 6. Add a command to this chapter’s case study…
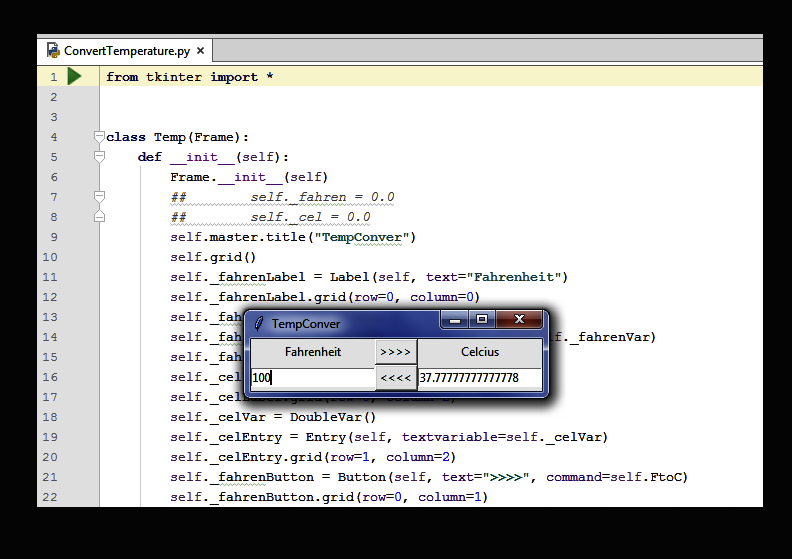
[SOLVED] FUNDAMENTALS OF PYTHON CHAPTER 8 PROJECT 1 2 3: These projects must be done in the latest version of IDLE: Also, please label and add brief comments to lines…
[SOLVED] PYTHON ASSIGNMENT SUM PRODUCT AVERAGE OF THE NUMBERS: Write a program that receives a series of numbers from the user and allows the user to press the enter key…


![[SOLVED] SEC370 LAB 5 POLICY PAPER: Review the Network Attacks tutorial in the lecture.](https://grademerit.com/wp-content/uploads/edd/2024/01/Screenshot-2024-01-23-022912.png)
![[SOLVED] SEC370 LAB 4 DISABLING UNNECESSARY SERVICES: Exercise 1 – Disabling Unnecessary Services In this exercise, you will disable unnecessary services for laptops that are taken by users outside of the corporate network. It is essential that unneeded network services are turned off to minimize the number of ports that are open when these mobile computers are connected to the public network such as the Internet.](https://grademerit.com/wp-content/uploads/edd/2024/01/Screenshot-2024-01-23-022506.png)
![[SOLVED] SEC370 LAB 3 YOU DECIDE ACTIVITY: Review the Public Key Infrastructure, Hashing and Digital Signatures, Cryptography: Public Key Encryption, and Cryptology tutorials in the lecture.](https://grademerit.com/wp-content/uploads/edd/2024/01/Screenshot-2024-01-23-021741.png)
![[SOLVED] SEC370 LAB 2 CREATE FIREWALL RULES: In this exercise, you will configure Inbound and Outbound Windows Firewall rules](https://grademerit.com/wp-content/uploads/edd/2024/01/Screenshot-2024-01-23-021220.png)
![[SOLVED] SEC370 LAB 1 YOU DECIDE: Perform reconnaissance on a target company of your choice using Google, their website, Whois, and nslookup to find out](https://grademerit.com/wp-content/uploads/edd/2024/01/Screenshot-2024-01-23-015556.png)
![[SOLVED] FUNDAMENTALS OF PYTHON CHAPTER 8 PROJECT 1 2 3: These projects must be done in the latest version of IDLE: Also, please label and add brief comments to lines of code.](https://grademerit.com/wp-content/uploads/edd/2024/01/Screenshot-2024-01-09-044812.png)
![[SOLVED] PYTHON ASSIGNMENT SUM PRODUCT AVERAGE OF THE NUMBERS: These projects must be done in the latest version of IDLE: Also, please label and add brief comments to lines of code.](https://grademerit.com/wp-content/uploads/edd/2024/01/Screenshot-2024-01-09-043926.png)